You are what your mobile says you are
Many features of devices can support biometric authentication methods
- |
- Written by Steve Cocheo
 Biometrics has been evolving to include not only what you are, as above, but what you do.
Biometrics has been evolving to include not only what you are, as above, but what you do.
What lesson does the McDonald’s Twitter account hack of mid-March have for banks exploring improvements to financial account authentication? That the days of the password being secure enough for much of anything appear to be coming to an end.
So suggests James Stickland, CEO of Veridium, a biometric identification firm, and formerly of HSBC and JP Morgan Chase.
“It’s a myth that the password and PIN are going to be enough,” says Stickland. “It’s enough today, but it won’t be tomorrow.” One of the main shortcomings, beyond the ease with which passwords and PINs can be found and faked, is that they don’t define the individual whose Twitter account, building access card, or bank account sits behind this “protection.” Ultimately, they are an access credential, but not a verification credential.
The McDonald’s embarrassment—someone hacked the corporation’s Twitter account and posted an insulting tweet about President Trump—is an illustration of the potentially high cost of something as seemingly innocuous as a social media login.
Who are you, really?
In the world of online authentication, there are three broad categories of identification: something you know, something you have, and something that you are.
Users of Apple and Google services will have noticed that these companies have begun using multiple contact points for accounts. Google, for instance, requires that Gmail users resetting their password involve a device other than their computer in the resetting process. Before the reset can be completed, for example, a user will receive a text on their previously registered handheld that must be input on the computer they are using to reset their password. The idea is that the legitimate person would have the device with them.
Biometrics comes in various forms, but the basic idea, broadly, is that the identifying item is something that the user not only has, but can’t transfer to another. A thief might get hold of both one’s handheld, and the code to unlock the screen, and then reset one’s password on an account. However—macabre mystery and sci-fi novels nothwithstanding—one’s fingers and other individually identifiable body parts generally stick around.
Veridium offers a patented “4 Fingers Touchless” identification method for mobile devices that uses the built-in camera to capture a detailed image of one of the user’s hands—specifically the fingerprint side of the four fingers, captured in one shot. (Rather than using a fingerprint pad, the technology relies on the image recorded by the camera—more ubiquitous than finger-reading handhelds.)
Earlier this year bunq—a European mobile-only bank based out of The Netherlands—adopted Veridium’s “4 Fingers Touchless” as an option for its customers. In a webinar presented earlier this year, David van Damme, head of partnerships and business development for bunq, said that 78% of its users selected this option for identification.
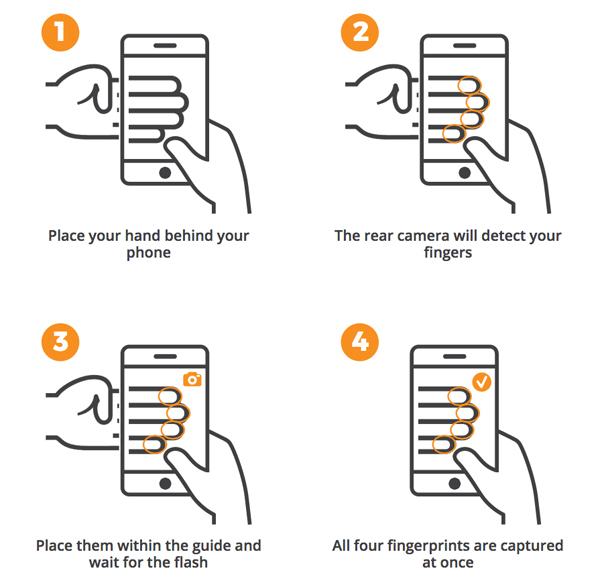
How the 4 Fingers Touchless method works, from a Veridium backgrounder.
He said that a small number of customers still prefer a method that uses “selfies,” a method that the young bank would like to eliminate over time. One reason for the bank’s preference is that bunq believes that a quick authentication shoot of the fingers when using a bunq service on a handheld will be more subtle. By comparison, shooting a selfie in a payment or similar situation can be somewhat awkward, according to van Damme. Using the fingers method is also considered more reliable because the ability to match selfies can vary according to lighting conditions. Veridium’s service, by contrast, is intended to be used with the mobile device’s flash.
Considering behavioral biometrics
Yet there is more to biometrics than simply the physical properties of a given human body. If that form of biometrics is “something you are,” then behavioral biometrics is “something you do,” or, even more specifically, “the way you do something.”
In an interview with Banking Exchange, Stickland explains that the versatile handheld device is full of features that can be used in different ways to establish and then verify identifying information.
For example, while it has long been possible to establish patterns of keystrokes on keyboarded devices, Stickland points out that today’s gadgets can also distinguish the pattern of pressure that an individual applies to a particular character versus another. This adds further dimensions for verifying who is using a device.
Today’s mobile devices also can determine how someone holds the device when in use—remember, one popular app is a phone-based equivalent of a multi-directional spirit level. Geolocation services add another dimension, indicating where someone is using their device. This can be logged and used for later comparison. Similarly, the IP address of a wifi spot being accessed by a mobile user tapping a local connection can be compared to past usage patterns.
Essentially, Stickland says, service providers can determine if it is likely that someone would be making a charge from a particular Starbucks. Have they ever accessed wifi from that shop before?
Of course, some of these factors are dynamic—a favorite spot when one is on vacation, for example. And Stickland explains that some of these factors fall into ranges. Sometimes, he says, “the ranges can be somewhat of a challenge.”
The capture of such data is ongoing, Stickland says, and companies using the information for identity verification would tend to establish benchmarks for each customer.
Adding techniques using these technologies help “make the walls higher and thicker,” says Stickland.
Stickland says it will be some time before the typical American banking customer sees much use of behavioral biometrics. “Behavioral biometrics is quite immature in the U.S.,” he says. He says the technology is “in its first innings in the U.S., and in its second innings in Europe.”
Tagged under Payments, Risk Management, Mobile, Cyberfraud/ID Theft, Feature, Feature3,













