Carbanak cyber gang steals $1 billion from banks
Up to 100 banks victimized in dozens of countries—and cyber scheme remains active
- |
- Written by John Ginovsky
 Following John Ginovsky’s report on the basics about the Carbanak cyber robbery, we offer links to related resources. That is followed by a roundup of experts’ views on this major theft.
Following John Ginovsky’s report on the basics about the Carbanak cyber robbery, we offer links to related resources. That is followed by a roundup of experts’ views on this major theft.
Up to $1 billion was stolen in about two years from financial institutions worldwide through an unprecedented cyber robbery recently detected by Kaspersky Lab.
INTERPOL, Europol, and authorities from different countries have combined efforts to uncover the criminal plot behind the unprecedented heists.
Experts report that responsibility for the robbery rests with a multinational gang of cyber criminals from Russia, Ukraine, and other parts of Europe, as well as from China.
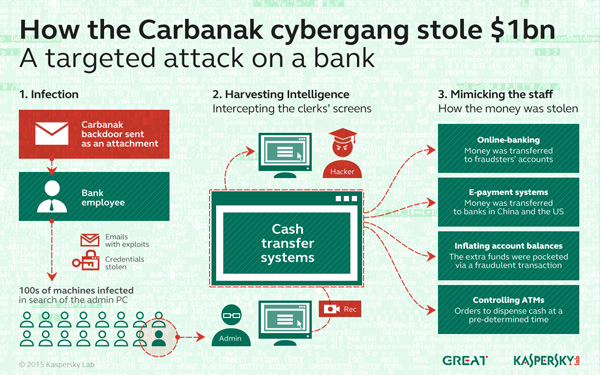
The Carbanak criminal gang responsible for the cyber robbery used techniques drawn from the arsenal of targeted attacks. The plot marks the beginning of a new stage in the evolution of cyber criminal activity, where malicious users steal money directly from banks, and avoid targeting end users.
The Carbanak malware was initially based on Carberp trojan software, though more recent versions do not use any of the Carberp software, according to Kaspersky Lab.
Details of Carbanak methodology
Since 2013, the criminals have attempted to attack up to 100 banks, e-payment systems, and other financial institutions in 25 or more countries. The attacks remain active.
Kaspersky Lab reports that the Carbanak targets included financial organizations in Russia, United States, Germany, China, Ukraine, Canada, Hong Kong, Taiwan, Romania, France, Spain, Norway, India, the United Kingdom, Poland, Pakistan, Nepal, Morocco, Iceland, Ireland, Czech Republic, Switzerland, Brazil, Bulgaria, and Australia.
[The American Bankers Association and the Financial Services Information Sharing and Analysis Center disputed the involvement of U.S. banks. The Financial Services Roundtable made a similar comment to The Wall Street Journal, as cited on the group’s website. Yesterday the FBI and Secret Service issued a "Private Industry Notification" regarding the situation. "PIN" notifications are not intended for media publication. Banks are advised to contact their trade associations for any details.]
The largest sums were grabbed by hacking into banks and stealing up to $10 million in each raid. Each robbery took between two and four months, on average, from infecting the first computer at the bank’s corporate network to making off with the stolen money.
The cyber criminals began by gaining entry into an employee’s computer through “spear phishing,” infecting the victim with the Carbanak malware. (Spear phishing uses typical phishing techniques, but involves an attack of a specific institution.)
They were then able to jump into the internal network and track down administrators’ computers for video surveillance. This allowed them to see and record everything that happened on the screens of staff who serviced the cash transfer systems.
In this way the fraudsters got to know every last detail of the bank clerks’ work and were able to mimic staff activity in order to transfer money and cash out.
How crooks got hands on cash
When the time came to cash in on their activities, the fraudsters used online banking or international e-payment systems to transfer money from the banks’ accounts to their own. In the second case the stolen money was deposited with banks in China or America. The experts do not rule out the possibility that other banks in other countries were used as receivers.
In other cases cybercriminals penetrated right into the very heart of the institutions’ accounting systems, inflating account balances before pocketing the extra funds via a fraudulent transaction. For example: If an account has $1,000, the criminals change its value so it has $10,000—and then transfer $9,000 to themselves. The account holder doesn’t suspect a problem because the original $1,000 balance is still there.
In addition, the cyber thieves seized control of banks’ ATMs and ordered them to dispense cash at a predetermined time. When the payment was due, one of the gang’s henchmen was waiting beside the machine to collect the “voluntary” payment.
“These bank heists were surprising because it made no difference to the criminals what software the banks were using. So, even if its software is unique, a bank cannot get complacent. The attackers didn’t even need to hack into the banks’ services: once they got into the network, they learned how to hide their malicious plot behind legitimate actions. It was a very slick and professional cyber robbery,” says Sergey Golovanov, principal security researcher at Kaspersky Lab’s Global Research and Analysis Team.
Sanjay Virmani, director of the INTERPOL Digital Crime Centre, noted that the Carbanak attacks “underline the fact that criminals will exploit any vulnerability in any system. It also highlights the fact that no sector can consider itself immune to attack and must constantly address their security procedures.”
Resources
• Read the full Kaspersky Lab report: Carbanak Apt: The Great Bank Robbery
• Learn more details about the “Carbanak” operation by reading the blog post available on Securelist
Roundup: What the experts are saying
Many security experts responded quickly to the Carbanak news. The following is a sample:
• Kevin Mitnick, KnowBe4's chief hacking officer:
"Even after 20 years, social engineering is still the easiest way into a target's network and systems, and it's still the hardest attack to prevent."
• Stu Sjouwerman, KnowBe4's CEO:
"While this cyber heist is considered very sophisticated, spear-phishing is one of the most preventable and affordable [infiltrations]. You would expect the finance industry to set the bar very high and have employees trained within an inch of their lives not to fall for such an attack. We would highly encourage financial institutions to take a look at their training methods and beef them up accordingly.”
• Mike Lloyd, CTO at RedSeal, a security analytics company:
“These thefts are a significant evolution in approach, since the attackers didn't simply break in, take over accounts, and run with the money. The time invested by criminals in studying the operations of target banks shows two things: First, that such attacks are lucrative enough for this time commitment to be worthwhile, and second, they would not have bothered if they did not have to.
“The lesson for defenders is clear: We need to up our game, understanding how we can be spied upon, and how motivated adversaries can work to hide in plain sight. This requires security teams to understand normal operations in great detail, including mapping out the environment and understanding how the infrastructure supports the business.
“This sounds easy enough, but in practice is fiendishly difficult—the rate of change of modern business makes it impossible to keep up without automated mapping and discovery of defensive gaps. Employees will always be prone to being fooled, as they were at the victim banks in this case. Organizations need to strengthen internal network segmentation, so that the whole chain does not fail whenever one weak link—usually a human—gets caught out.”
• Jerome Segura, senior security researcher at Malwarebytes Labs:
“This is possibly one of the largest cyber bank heists in history which happened under the noses of many banks worldwide. However, the threat, dubbed Carbanak, is not particularly sophisticated as earlier reports may have indicated. The attackers did not use a zero day vulnerability but rather social engineered bank employees with a phishing email.
“For several months Carbanak was active on internal systems and also spread laterally to map out the banks' infrastructure.
“End-point security with anti-malware combined with anti-exploit technology is a very important barrier that is often forgotten. Of course because employees are an element that is often taken advantage of, training as well as access controls are crucial to avoid giving someone access to certain parts of the networks that they should not be allowed to view. An attacker may not need to use cutting-edge malware or exploits to achieve his goals. Careful planning and execution is enough to take advantage of severe security holes that unfortunately still exist in large financial institutions.
“One key component was its ability to record user activity, which included a video feed of employees' actions. This allowed the attackers to train and learn about the way financial institutions worked so that they would be ready for the eventual heist. …
“This operation has been going on for quite some time and is likely still active. One of the reasons for its success is the attacker's ability to infiltrate bank's networks with relative ease.
• Steve Hultquist, chief evangelist at RedSeal, a security analytics company:
“The magnitude of this theft underscores today's reality: cyber attacks are ongoing, long-running, automated, and varied. It is simply not possible for anyone to know all of the possible ways that a network may be used to attack an organization to steal and destroy. These banks invested in security, have experts involved in protecting their assets, and they certainly know the importance of defenses.
“However, the complexity and ongoing change in the environment makes tracking possible attacks impossible without automation to anticipate and prevent attack in addition to the reactive defenses that are more common. It's time for organizations to defend their networks with more comprehensive automation than attacks use to find the weaknesses. It's the only way to turn the tables.”
• Dwayne Melancon, CTO of Tripwire:
"This is a jarring reminder of how easy it is for even sophisticated enterprises to overlook damaging changes to their cyber infrastructure. Malware leaves a trace when it compromises a system—even custom malware. Unfortunately, most of the times, that mark goes unnoticed because enterprises haven't established a baseline, or known good state, and aren’t continuously monitoring for changes to that baseline.
“Not only does this lack of awareness make it easier for criminals to gain a foothold, it makes it difficult, time-consuming, and very expensive to determine which systems can be trusted after-the-fact, and to determine how to remove the contaminated systems from the network.
“This should be a wakeup call for enterprises to take a step back and make sure they nail the fundamentals: maintain an accurate inventory of all the devices and applications on your network; reduce your attack surface by ensuring that all your systems and applications are configured securely according to a well-vetted security standard; scan for and patch any known vulnerabilities; and continuously monitor for changes and unusual behavior within your network."
• Branden Spikes, CEO and founder of Spikes Security:
"This is a prime example of risks enterprises take when they allow employees to browse the web, particularly from administrative workstations with access to valuable assets. With attacks like these easily evading detection, this attack serves as a stark reminder that it's unwise to shift the focus from prevention onto reactive things like information sharing …, detection, or faster response. Policymakers and cyber security chiefs need to put more emphasis on prevention. Investments in prevention technologies like browser isolation, and blocking the malignant and pervasive browsers from directly reaching websites from sensitive parts of the network will go a long way to stop these attacks in the future."
Tagged under Technology, Risk Management, Cyberfraud/ID Theft, Feature, Feature3,