Security pros flunk cybersecurity
Simultaneously, they grade themselves well in handling detected threats
- |
- Written by John Ginovsky
 “Devops” and “containerization platforms” are two areas that really flummox security experts. Both are brand new challenges.
“Devops” and “containerization platforms” are two areas that really flummox security experts. Both are brand new challenges.
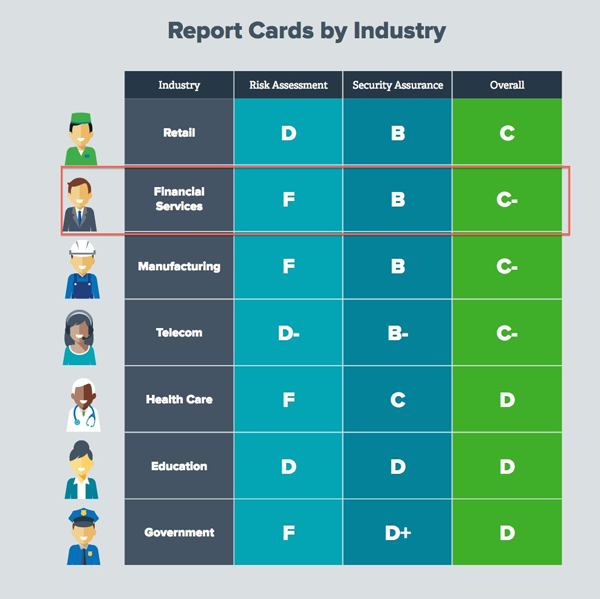
Financial services’ corporate security practitioners give themselves an “F” in being able to assess cybersecurity risks, according to an influential survey by Tenable Network Security Inc.
At the same time, though, they give themselves a “B” in their confidence in being able to deal with cybersecurity threats—once they have been discovered.
The 2017 Global Cybersecurity Assurance Report Card by Tenable provides a means to take the temperature of security experts in many different industries in nine countries. Surveyers canvassed 700 companies each employing 1,000 people or more. Of these companies, 37% were located in the U.S.
Broad confidence measure declines
Overall, the global cybersecurity confidence index fell six points compared to the previous survey, earning an overall score of 70%—a “C-minus” on the report card.
The overall decline in confidence is the result of a 12-point drop in the risk assessment index, which measured the ability of respondents to assess cyber risk across 11 key components of the enterprise information technology landscape.
“Today’s network is constantly changing—mobile devices, cloud, IoT, web apps, containers, virtual machines—and the data indicate that a lot of organizations lack the visibility they need to feel confident in their security posture,” says Cris Thomas, strategist, Tenable Network Security, in an interview with Banking Exchange.
What financial services companies say
But all is not doom and gloom.
In the financial services category, granted, respondents gave themselves a “D-plus” for laptop and notebook security and an “F” in desktop computer security. However, they gave themselves a “B” in being able to deal with threats once they are known.
“In financial services, they seem to be unsure where the threats are but they are very confident that once they find them they can mitigate them. That’s a good thing,” according to Thomas.
Detail from Tenable’s infographic about the survey comparing participating industries’ self-assessments. For the entire infographic, please click on the image.
Thomas put the report card in perspective.
“You have to remember that this is looking at the confidence of the individuals’ ability to address these risks,” he says. “This is a feeling, a perception, their beliefs of what their networks and organizations are capable of doing.”
Still, it is instructive to look at the specific areas in which security officers feel least able to assess. In financial services, they saw themselves flunking in dealing with risks from cloud environments, physical and digital servers, and desktops. Only slightly better, at a grade of “D”, were their ability to deal with laptops/notebooks, mobile devices, network infrastructure, network perimeters, and web applications.
“Mobile and cloud, we are just starting now getting a handle on them, even though they’ve been around for several years,” Thomas says.
Two fast-tracks where failure ranks
But that pales in comparison with two really new issues that security professionals are just now facing: “devops” (short for development and operations) and “containerization platforms.”
These weren’t even a category in last year’s report card survey. This year, though, security officials gave themselves a solid “F” in assessing their risk.
In practical terms, these both refer to accelerated ways that software developers can come up with new and/or improved business applications that can hasten their speed into a given market.
Devops, Thomas says, can be pictured as having multiple virtual machines or applications in development running on a single piece of hardware and using entire operating systems.
Containerization platforms are similar, only instead of having entire operating systems for the applications in development, they only use the bits and parts of it that those applications need. Thus, app developers can run many containers on one piece of hardware.
“Why this is a security issue is that if you don’t look at security issues when you build a container, then any vulnerabilities that are in the bits of the operating system when the code is created are then shipped in that container when it is deployed. They are very difficult to fix after the fact,” Thomas says. “Containers are really new. Brand new. Devops is also a brand new type of thing.”
Cause for optimism
On the flip side, those in financial services are very optimistic about dealing with security issues. They give themselves “Bs” in: measuring security effectiveness, viewing network risks continuously, aggregating risk intelligence, aligning security with business, conveying risks to executives and board members, and having executive and board member commitment.
“Security professionals are still able to maintain their optimism and are looking forward to next year, saying, ‘Yes, we’re going to be able to do better. Yes, we’re going to be able to mitigate these threats’,” says Thomas. “They are not suffering from depression and wallowing in their offices. They are able to keep their heads up and plug away.”
Essentials for financial services security
Looking forward, Thomas notes that companies need to stick to security basics. Essentially, he breaks these into:
• Know what data you have—“Inventory all your hardware and all your software, all your virtual machines, your cloud. Know where your data is. Know where your really important data is and where your not-so-important data is.”
• Have a plan to protect it—“Make sure you have a balanced approach to security. If you have different products from different vendors, that’s fine, but make sure they all talk to each other. Make sure you have an ecosystem where everything works together and that you are prioritizing your risks. Then you can get actionable insight from the data that you’re getting from the tools that you apply.”
• Establish a way to measure success—“How do you measure whether or not your plan is succeeding? You need to define some metrics in your environment, to say, ‘Okay, this number went up, this number went down, what does that mean to me and my organization? Am I succeeding in my security plan?’”
“Those are just some of the basic things you want to look at moving forward,” says Thomas, “so that next year, when we do this survey again, we’ll get some better numbers.”
Download Tenable’s 2017 Global Cybersecurity Assurance Report Card [Registration required]
Tagged under Risk Management, Cyberfraud/ID Theft, Feature, Feature3,